In today's digital world, remotely access SSH web has become an essential tool for professionals, developers, and IT administrators who need secure access to remote servers. SSH (Secure Shell) provides a robust solution for encrypted communication between devices, ensuring data integrity and security. Whether you're managing servers, accessing files, or deploying applications remotely, understanding SSH is crucial.
With the increasing demand for remote work and cloud-based infrastructure, mastering SSH remote access can significantly enhance your productivity and efficiency. This guide will walk you through everything you need to know about SSH, including setup, best practices, troubleshooting, and advanced configurations.
By the end of this article, you'll have a solid understanding of how to securely connect to remote servers via SSH, ensuring your data remains protected while maintaining seamless access to your systems.
Read also:Man City Vs Chelsea A Thrilling Rivalry In The Premier League
Table of Contents
- Introduction to SSH
- How SSH Works
- Setting Up SSH
- Remotely Access SSH Web
- Security Best Practices
- Advanced SSH Configurations
- Troubleshooting SSH
- Common SSH Commands
- SSH and Web Applications
- Conclusion
Introduction to SSH
SSH, or Secure Shell, is a cryptographic network protocol that facilitates secure communication between two devices over an unsecured network. It is widely used for remote server management, file transfers, and tunneling. Unlike other protocols, SSH encrypts all data transmitted between devices, making it an ideal choice for sensitive operations.
Developed in the early 1990s, SSH has evolved into a critical component of modern IT infrastructure. Its primary purpose is to provide a secure channel for remote access, ensuring that credentials, commands, and data remain private and tamper-proof.
For professionals who need to remotely access SSH web, understanding the fundamentals of SSH is essential. This includes learning about its architecture, protocols, and how it integrates with web-based applications.
How SSH Works
SSH operates by establishing a secure connection between a client and a server. The process begins with authentication, where the client proves its identity to the server. Once authenticated, SSH creates an encrypted session, ensuring that all communication remains private.
Here’s a breakdown of how SSH works:
- Authentication: Users can authenticate using passwords, public keys, or other methods.
- Encryption: SSH uses symmetric encryption algorithms to secure data transmission.
- Data Integrity: A hash function ensures that data remains unaltered during transmission.
Understanding these mechanisms is crucial for anyone looking to remotely access SSH web. By leveraging SSH's built-in security features, you can protect your systems from unauthorized access and data breaches.
Read also:Understanding Federal Reserve Interest Rates A Comprehensive Guide
Setting Up SSH
Installing SSH
Before you can remotely access SSH web, you need to ensure that SSH is installed on both the client and server. Most Linux distributions come with SSH pre-installed, but you may need to install it manually on other operating systems.
For Linux users, you can install SSH using package managers like apt or yum. On Windows, you can use tools like OpenSSH or third-party clients such as PuTTY.
Here’s a quick guide to installing SSH:
- On Ubuntu:
sudo apt-get install openssh-server - On CentOS:
sudo yum install openssh-server - On Windows: Download and install OpenSSH from the Microsoft Store.
Configuring SSH
After installation, the next step is configuring SSH to suit your needs. This involves editing the SSH configuration file, typically located at /etc/ssh/sshd_config. Key configurations include:
- Changing the default port (e.g., from 22 to a custom port).
- Disabling password authentication in favor of public key authentication.
- Restricting access to specific IP addresses or users.
By properly configuring SSH, you can enhance security and streamline your workflow when remotely accessing SSH web.
Remotely Access SSH Web
Once SSH is installed and configured, you can begin remotely accessing SSH web. This involves connecting to a remote server using an SSH client. The basic command for connecting to a server is:
ssh username@server_ip_address
For example, if your username is "admin" and the server's IP address is "192.168.1.100," the command would be:
ssh admin@192.168.1.100
When connecting to a web server, you may need to use additional configurations to ensure compatibility. This includes setting up firewalls, configuring reverse proxies, and enabling SSH tunneling.
Security Best Practices
Security is paramount when remotely accessing SSH web. To protect your systems from potential threats, follow these best practices:
- Use Strong Passwords: Avoid using common passwords or easily guessable phrases.
- Enable Two-Factor Authentication (2FA): Add an extra layer of security by requiring a second form of verification.
- Restrict Access: Limit SSH access to trusted IP addresses or networks.
- Regularly Update Software: Keep your SSH client and server software up to date to patch vulnerabilities.
By adhering to these practices, you can significantly reduce the risk of unauthorized access and data breaches.
Advanced SSH Configurations
SSH Tunneling
SSH tunneling allows you to securely access services running on a remote server. This is particularly useful when remotely accessing SSH web, as it encrypts all traffic between your local machine and the server.
To set up an SSH tunnel, use the following command:
ssh -L local_port:destination_host:destination_port username@server_ip_address
For example, to access a web server running on port 80, you could use:
ssh -L 8080:localhost:80 admin@192.168.1.100
Port Forwarding
Port forwarding is another advanced SSH feature that allows you to redirect traffic from one port to another. This is useful for bypassing firewalls or accessing services that are blocked by network restrictions.
To enable port forwarding, use the following command:
ssh -D local_port username@server_ip_address
This command sets up a SOCKS proxy on the specified local port, allowing you to route traffic through the SSH connection.
Troubleshooting SSH
Despite its robustness, SSH connections can sometimes fail due to various reasons. Common issues include:
- Connection Refused: Ensure that the SSH service is running on the server and that the firewall allows incoming connections.
- Authentication Failed: Verify that your username, password, or key file is correct.
- Timeout Errors: Check your network connection and ensure that there are no routing issues.
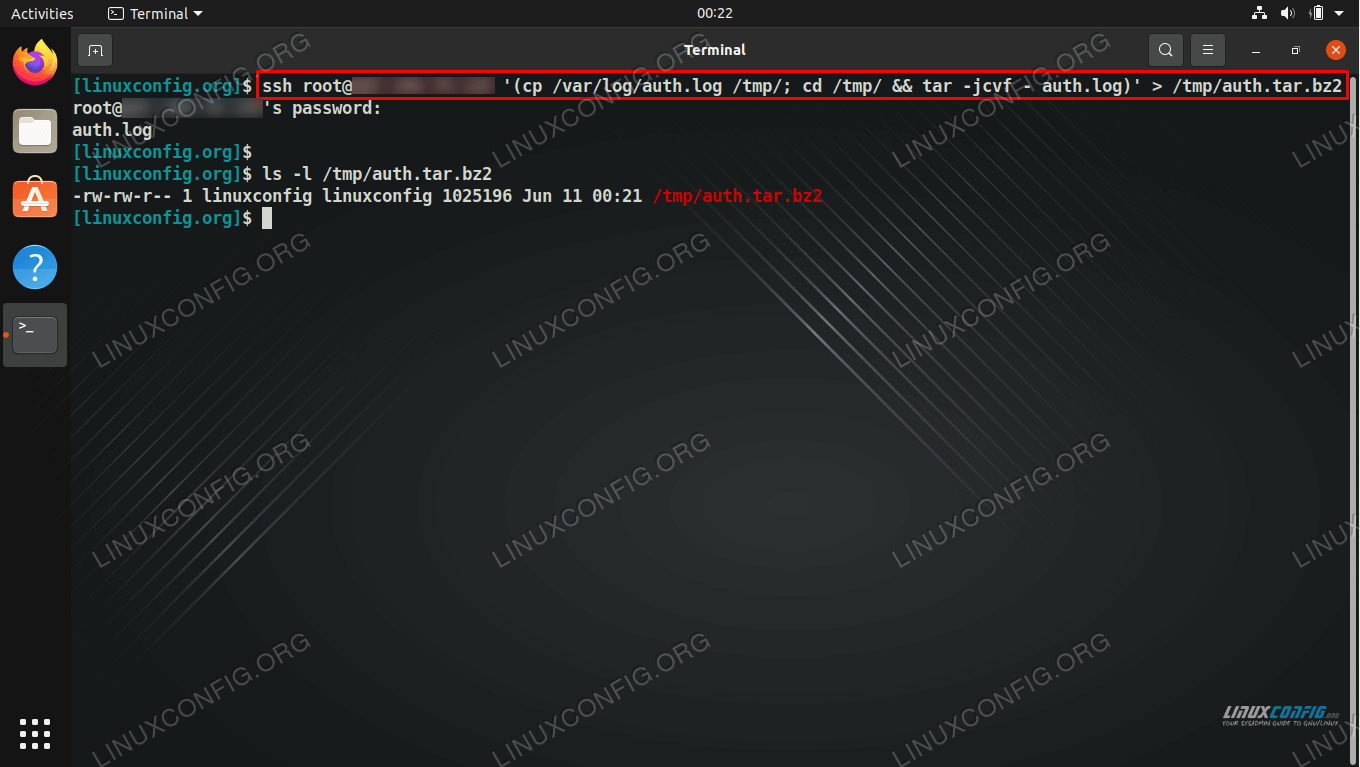
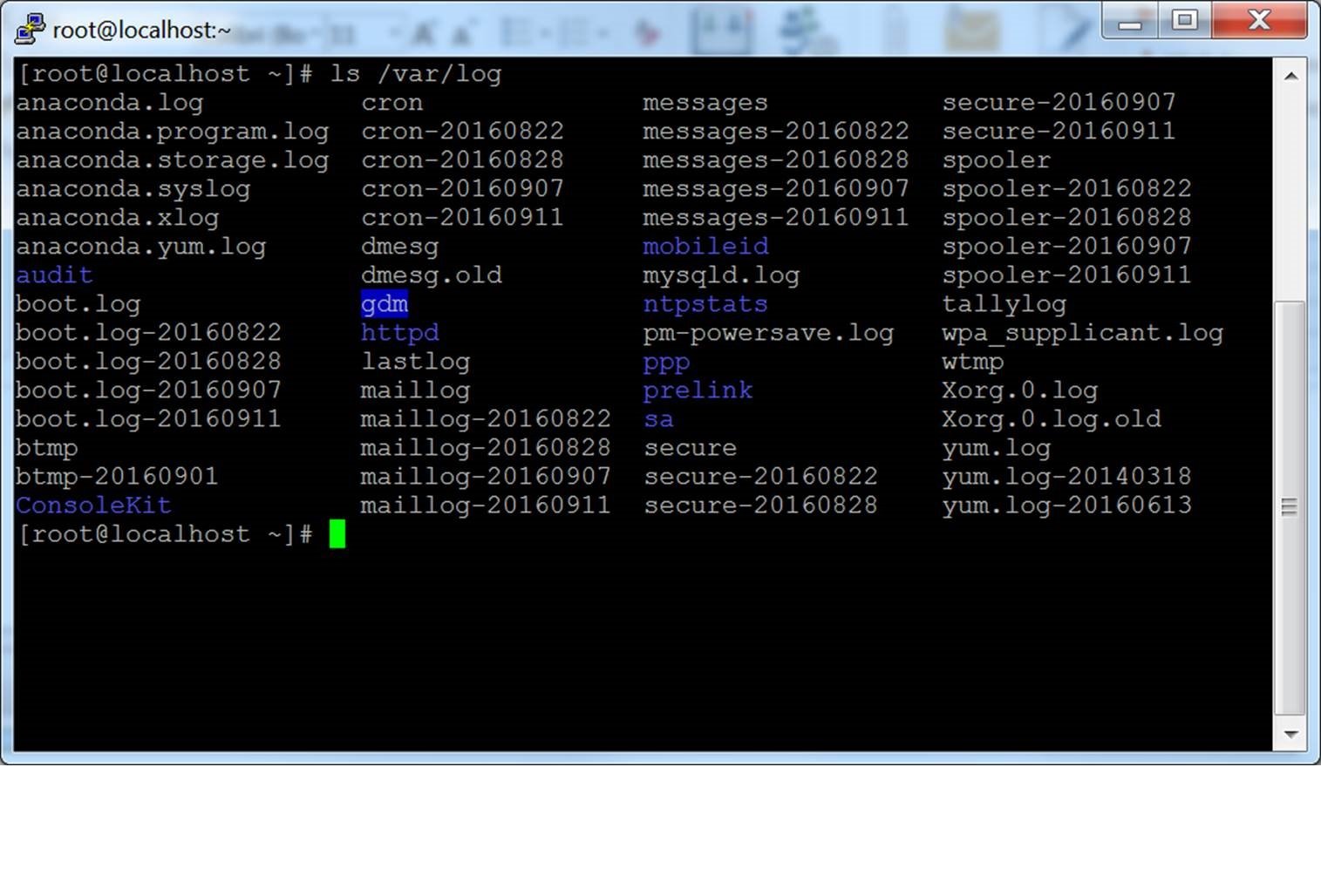
If you encounter any of these problems, consult the SSH logs for more information. These logs are typically located at /var/log/auth.log on Linux systems.
Common SSH Commands
Here are some common SSH commands that you may find useful when remotely accessing SSH web:
ssh username@server_ip_address: Connect to a remote server.scp file_name username@server_ip_address:/path/to/destination: Copy files to a remote server.ssh-keygen: Generate SSH keys for public key authentication.ssh-copy-id username@server_ip_address: Copy your public key to a remote server.
Mastering these commands can greatly enhance your productivity and efficiency when working with SSH.
SSH and Web Applications
SSH plays a critical role in web development and deployment. By leveraging SSH, developers can securely manage servers, deploy applications, and troubleshoot issues. Additionally, SSH can be used to set up secure tunnels for database connections, API calls, and other web-related tasks.
For example, you can use SSH to:
- Automate deployments using tools like Ansible or Fabric.
- Securely access databases running on remote servers.
- Monitor server performance and logs in real-time.
By integrating SSH into your workflow, you can streamline your development processes and improve overall security.
Conclusion
In conclusion, mastering how to remotely access SSH web is essential for anyone working in IT, development, or server management. By understanding the fundamentals of SSH, setting it up correctly, and following best practices, you can ensure secure and efficient remote access to your systems.
We encourage you to experiment with the concepts discussed in this article and explore advanced configurations to further enhance your skills. If you found this guide helpful, please share it with others or leave a comment below. Additionally, feel free to explore our other articles for more insights into web development and IT security.
Stay secure, stay connected!