SSH RemoteIoT on Raspberry Pi has become an essential tool for developers and hobbyists alike who want to manage and control their IoT projects remotely. Whether you're setting up a home automation system or running a complex network of sensors, understanding SSH and its application in IoT can significantly enhance your project's capabilities. This guide will provide you with a detailed overview of how to leverage SSH for remote IoT management using Raspberry Pi.
In today's interconnected world, the Internet of Things (IoT) continues to grow at an exponential rate. As more devices become connected, the need for secure and efficient remote management solutions has never been greater. SSH RemoteIoT on Raspberry Pi offers a reliable and secure way to interact with your IoT devices from anywhere in the world.
This article will walk you through the basics of SSH, how it works with Raspberry Pi, and advanced techniques for managing IoT projects. By the end of this guide, you'll have a solid understanding of SSH RemoteIoT on Raspberry Pi and be equipped with the knowledge to implement it in your own projects.
Read also:Kraken Vs Wild Unveiling The Epic Battle Of Marine Legends
Table of Contents
- Introduction to SSH
- Raspberry Pi Overview
- SSH RemoteIoT Setup
- Securing Your SSH Connection
- Common SSH Commands
- Advanced SSH Techniques
- Troubleshooting SSH Issues
- SSH and IoT Integration
- Best Practices for SSH RemoteIoT
- Conclusion and Next Steps
Introduction to SSH
Secure Shell (SSH) is a cryptographic network protocol that allows users to securely access and manage remote systems over an unsecured network. SSH ensures data integrity, confidentiality, and authentication between two networked devices. When it comes to IoT projects, SSH RemoteIoT on Raspberry Pi serves as a powerful tool for managing devices remotely.
Key Features of SSH:
- Encryption: All data transmitted via SSH is encrypted, ensuring secure communication.
- Authentication: SSH supports various authentication methods, including passwords and public key authentication.
- Portability: SSH is available on a wide range of operating systems, making it versatile for cross-platform use.
By leveraging SSH RemoteIoT on Raspberry Pi, you can perform tasks such as file transfers, remote command execution, and system monitoring without the need for physical access to the device.
Raspberry Pi Overview
The Raspberry Pi is a popular single-board computer designed for educational and hobbyist use. Its affordability, versatility, and open-source nature make it an ideal platform for IoT projects. With its GPIO pins, network connectivity, and support for various operating systems, the Raspberry Pi can be easily configured to act as a central hub for IoT devices.
Key Specifications of Raspberry Pi:
- Processor: Broadcom BCM2711, Quad-core Cortex-A72 (ARM v8) 64-bit SoC @ 1.5GHz
- RAM: 2GB, 4GB, or 8GB LPDDR4-3200 SDRAM
- Connectivity: Dual-band 2.4GHz and 5GHz IEEE 802.11ac wireless, Bluetooth 5.0, BLE
- Storage: MicroSD card slot for loading operating system and data storage
When combined with SSH, the Raspberry Pi becomes a robust solution for remote IoT management, enabling users to control and monitor devices from anywhere.
Read also:Mount Rushmore Presidents The Iconic Monument And The Men Who Shaped A Nation
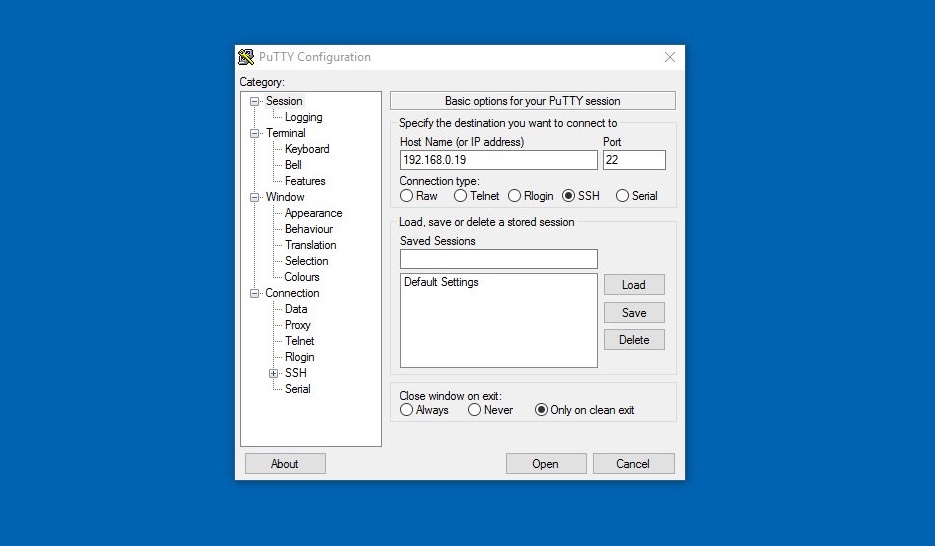
SSH RemoteIoT Setup
Step-by-Step Guide to Enabling SSH on Raspberry Pi
Enabling SSH on your Raspberry Pi is a straightforward process that can be done either through the graphical user interface or the command line. Below is a step-by-step guide to help you get started:
- Power off your Raspberry Pi and insert the microSD card into your computer.
- Create an empty file named "ssh" (without any file extension) in the boot partition of the microSD card.
- Reinsert the microSD card into your Raspberry Pi and power it on.
- Use a network scanner tool like Advanced IP Scanner to find the IP address of your Raspberry Pi.
- Open an SSH client (such as PuTTY for Windows or Terminal for macOS/Linux) and connect to the Raspberry Pi using the IP address and default credentials (username: pi, password: raspberry).
Once connected, you can begin configuring your Raspberry Pi for IoT applications and managing it remotely using SSH.
Securing Your SSH Connection
Best Practices for SSH Security
While SSH provides a secure method for remote access, it's important to implement additional security measures to protect your Raspberry Pi and IoT devices from unauthorized access. Below are some best practices for securing your SSH connection:
- Change Default Credentials: Update the default username and password to something unique and complex.
- Disable Root Login: Restrict root access to prevent unauthorized users from gaining administrative privileges.
- Use Public Key Authentication: Replace password-based authentication with public key authentication for added security.
- Limit Access by IP Address: Configure the SSH server to only accept connections from specific IP addresses.
- Update Regularly: Keep your Raspberry Pi's operating system and software up to date to patch any security vulnerabilities.
Implementing these security measures will help safeguard your SSH RemoteIoT on Raspberry Pi setup against potential threats.
Common SSH Commands
Understanding the most commonly used SSH commands is essential for effectively managing your Raspberry Pi and IoT devices. Below are some of the key commands you'll need:
ssh pi@: Connect to your Raspberry Pi using SSH.scp file.txt pi@: Transfer files between your local machine and Raspberry Pi.:/home/pi/ sudo apt update && sudo apt upgrade: Update your Raspberry Pi's software packages.sudo systemctl restart ssh: Restart the SSH service on your Raspberry Pi.
These commands form the foundation of SSH RemoteIoT on Raspberry Pi management and will allow you to perform a wide range of tasks efficiently.
Advanced SSH Techniques
Tunneling and Port Forwarding
SSH tunneling and port forwarding are powerful techniques that allow you to securely access services running on your Raspberry Pi from remote locations. These methods are particularly useful for IoT projects where sensitive data is being transmitted.
Types of SSH Tunneling:
- Local Port Forwarding: Allows you to access a service on the remote server from your local machine.
- Remote Port Forwarding: Enables the remote server to access a service running on your local machine.
- Dynamic Port Forwarding: Acts as a SOCKS proxy, routing all traffic through the SSH connection.
By leveraging these advanced SSH techniques, you can enhance the functionality and security of your SSH RemoteIoT on Raspberry Pi setup.
Troubleshooting SSH Issues
Even with proper configuration, SSH connections can sometimes encounter issues. Below are some common problems and their solutions:
- Connection Refused: Ensure that the SSH service is running on your Raspberry Pi and that the firewall is not blocking the connection.
- Authentication Failed: Double-check your username and password or verify that your public key is correctly configured.
- Timeout Error: Check your network connection and ensure that the IP address of your Raspberry Pi is correct.
By addressing these common issues, you can maintain a stable and reliable SSH RemoteIoT on Raspberry Pi connection.
SSH and IoT Integration
Building a Remote IoT Control Center
With SSH RemoteIoT on Raspberry Pi, you can create a centralized control center for managing your IoT devices. By combining SSH with tools like MQTT, Node-RED, and Home Assistant, you can build a robust system for monitoring and controlling your IoT ecosystem.
Benefits of SSH in IoT:
- Secure communication between devices.
- Remote management capabilities.
- Scalability for large-scale IoT projects.
Whether you're managing a smart home or an industrial IoT network, SSH RemoteIoT on Raspberry Pi provides the tools you need to succeed.
Best Practices for SSH RemoteIoT
To get the most out of your SSH RemoteIoT on Raspberry Pi setup, consider the following best practices:
- Regular Backups: Ensure that your Raspberry Pi's configuration and data are regularly backed up to prevent data loss.
- Documentation: Keep detailed records of your SSH configurations and IoT setups for future reference.
- Monitoring: Use tools like fail2ban to monitor and block suspicious SSH login attempts.
By adhering to these best practices, you can maximize the efficiency and security of your SSH RemoteIoT on Raspberry Pi projects.
Conclusion and Next Steps
In conclusion, SSH RemoteIoT on Raspberry Pi offers a powerful and secure solution for managing IoT devices remotely. By following the guidelines and best practices outlined in this article, you can effectively implement SSH in your IoT projects and take advantage of its many benefits.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore our other articles for more insights into IoT and Raspberry Pi development. Together, let's continue to innovate and push the boundaries of what's possible with IoT technology.